SentinelOne Active EDR
ActiveEDR is an automated response that relies on artificial intelligence to take the burden off the IT team. IT teams can quickly understand the story and root cause behind each threat. The technology can autonomously attribute each event on the endpoint to its root cause without any reliance on cloud resources.
Why is it important?
Polymorphic Malware:
Malware that changes characteristics to slip past known signatures since there is a lag time between updates
Weaponized Documents:
Tricks AV scans since they only scan the doc and not the embedded script
Browser Drive-by Downloads:
Leverages browser or add-in exploits to download malware
Fileless Attacks:
Attacks that occur without installing a payload, typically in memory and uses the system’s built-in resources to execute code to infect or open firewall ports
Obfuscated Malware:
Hackers hiding or protecting malicious code within benign code, Encryption, or even playing dead with AV company’s Sandbox for discovering Malware
Zero-day Threats:
Unknown vulnerability or exploit before providers can issue updates
ROI/Cost Savings
Reduce IT overhead related to Malware/Ransomware
- Cloud Management
- System Imaging
- Fewer tickets/issues
Recovery from Ransomware
- Employee Time efficiency/productivity loss
- Outage and Restoration Time
- Loss of Data
- Investigating Time and Follow up Costs
- Company Brand Reputation
Benefits of Sentinel
Multi-Platform Protection, Single Pane of Glass
Low Administration Overhead from Alert Fatigue
Budget Friendly with High End Features
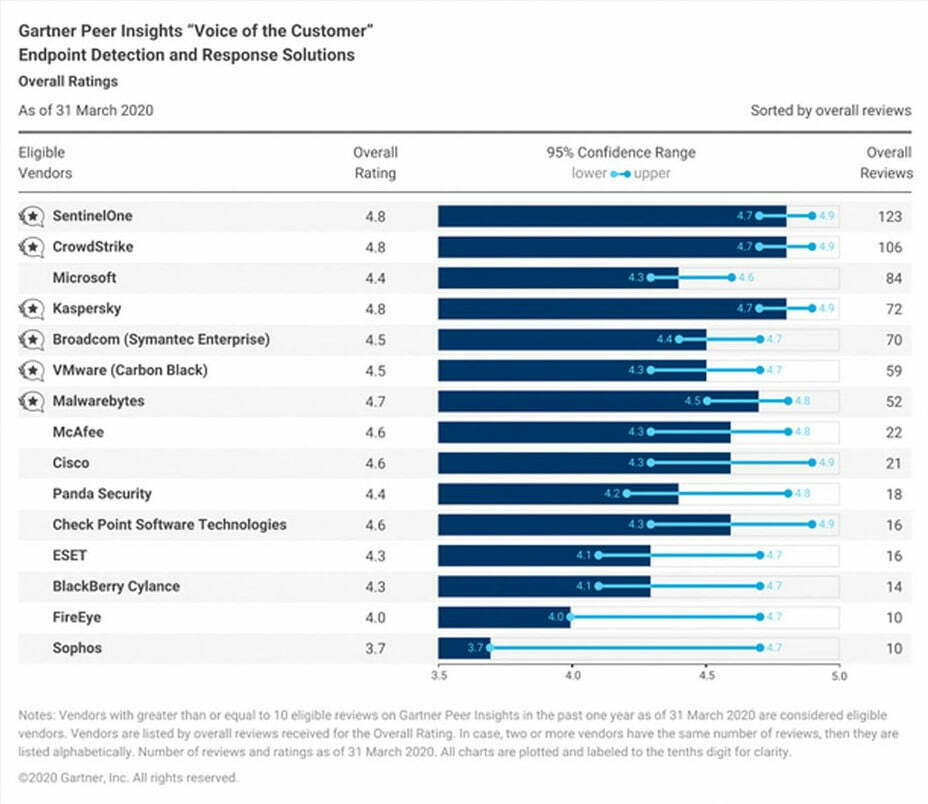
High Customer Satisfaction Gartner Ratings
7 Engine Behavior AI to stop threats undetectable by Signature based End-point Protections AVs
Integrated File Rollback/Recovery, reducing time and gaps in backups and restore processes
On-Agent Behavioral AI engines means real time and no cloud latency
Forensic Storyline and Threat Summary Reporting